Blog
NIS2 in the DACH Region: Why Identity & Access Management Is a 2025 Priority
A Comprehensive Guide for CISOs and Compliance Leads to Staying Ahead of NIS2 in Germany and Austria

30,000 German companies are now in NIS2’s crosshairs — most aren’t ready. The EU’s NIS2 Directive is no longer theory. It’s in force. And while Germany’s enforcement clock technically starts ticking in 2026, the reality is: Your audit trail, your access controls, and your leadership’s accountability will all be under scrutiny in 2025. In Austria, the pressure is even higher — enforcement is expected to begin by the end of this year. Meanwhile, identity and access management (IAM) has quietly become one of the most visible and enforceable compliance fronts. This article outlines what companies across the DACH region need to know — and how to use identity-centric data access governance as a core pillar of your compliance strategy.
🧠 Article Summary: What NIS2 Demands From You
NIS2 is already in force at the EU level. The directive applies to critical and digital sector companies with >50 employees or >€10M turnover — extending the coverage from ~2,000 organizations affected by NIS1 to ~30,000 organizations only in Germany.
At its core, NIS2 mandates:
- Robust cybersecurity controls (Article 21)
- Strict incident reporting timelines (early warning within 24 hours, initial assessment within 72 hours, and final report within 30 days)
- Regular testing of control effectiveness
- Executive accountability for failures
- Vendor and supply chain risk management
Identity & Access Management (IAM) is a major focus — from least privilege and access reviews to on-boarding/off-boarding and traceability.
To be prepared, CISOs in DACH should already now:
- Assess their exposure (Annexes I & II)
- Close IAM and incident response gaps
- Test and improve security controls
- Engage leadership and assign accountability
- Prepare documentation and registration
🧩 Bottom line: NIS2 moves cybersecurity from best practice to legal obligation. 2025 is your last full year to build readiness before enforcement hits.
💡 Introduction: What Is NIS2?
NIS2 is the EU’s updated cybersecurity law. It expands the scope of its predecessor NIS1 by requiring critical and digital service providers to implement a range of cybersecurity risk-management measures, including incident reporting, supply chain security, and robust identity and access governance.
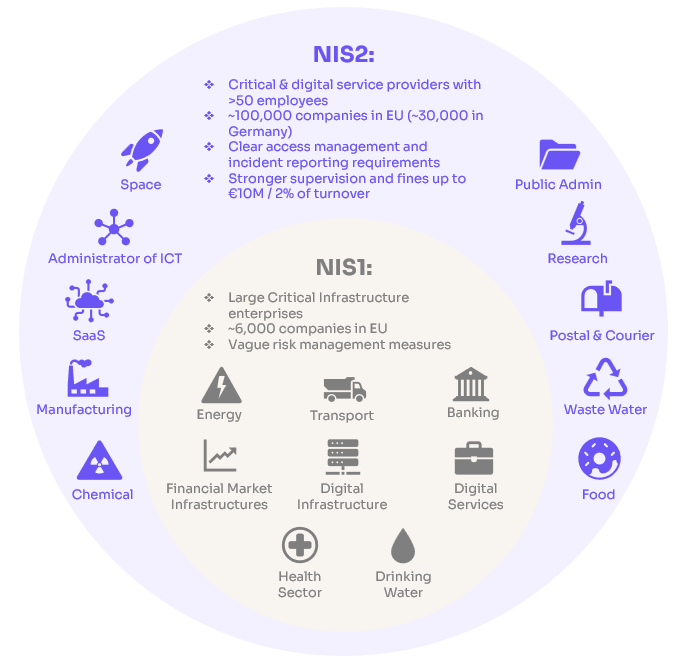
Figure 1: Key Differences Between NIS1 and NIS2
Key facts:
- Applies to organizations with >50 employees or >€10M turnover
- Covers 18 sectors (e.g. IT services, SaaS, health, finance, public administration)
- Introduces fines up to €10M or 2% of global turnover
- Sets strict timelines for incident reporting (24h/72h/30d)
🌍 NIS2 Rollout & Readiness in DACH
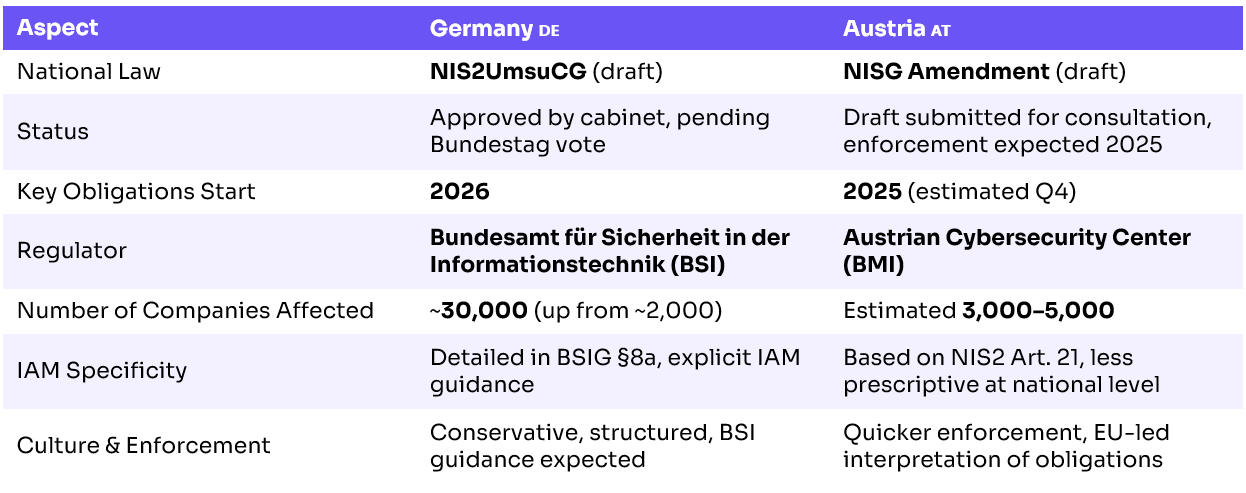
Table 1: Key Differences in NIS2 Implementation Between Germany and Austria
📌 Takeaway: While both countries fall under the EU NIS2 Directive, Germany and Austria differ in terms of legislative progress, enforcement timelines, and the specificity of identity and access management (IAM) guidance. CISOs operating in the DACH region should align to the stricter requirements and prepare for Austria’s potential earlier enforcement in Q4 2025.
While the legal enforcement of NIS2 in DACH is expected in 2026 (with potential earlier enforcement for Austria), most companies are still in early stages of implementation. The chart below shows readiness of German companies across core areas like training, incident response, crisis management, and supply chain security. As visible, less than one-third of organizations have fully implemented key controls — leaving significant ground to cover before NIS2 becomes enforceable.
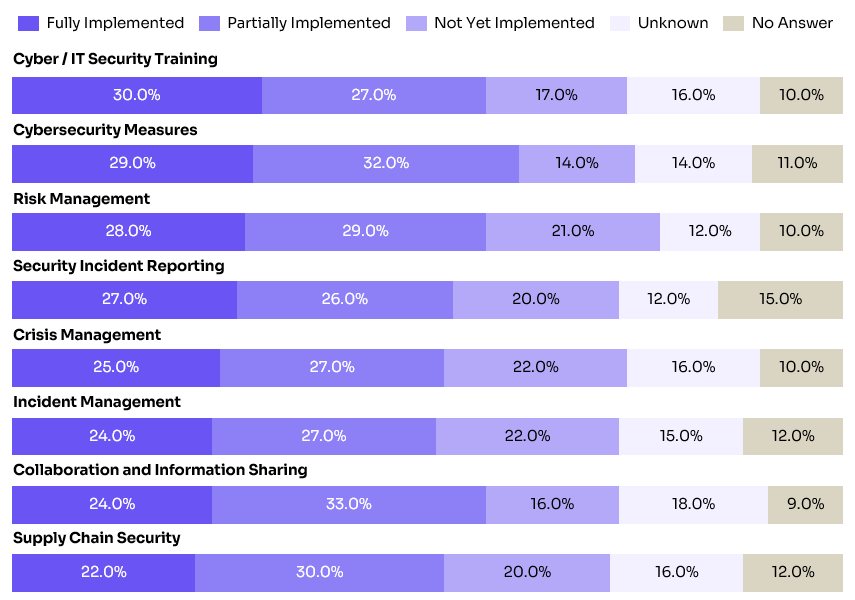
Figure 2: Degree of Implementation of NIS2 Requirements by Category in Germany (Source: TechConsult/Plusnet, June 2024, 200 companies surveyed)
🛡️ Key Cybersecurity Requirements for Organizations Under NIS2
At the heart of NIS2 is a set of baseline cybersecurity risk management measures that all in-scope entities must implement. Article 21 of the directive specifies that companies must take “appropriate and proportionate technical, operational and organisational measures to manage the risks” to their network and information systems and to “prevent or minimize the impact of incidents”. These measures must be state-of-the-art and risk-based, taking into account the company’s size, exposure, and the potential societal impact of incidents.
At a minimum, organizations need to address the following areas:
- Risk Analysis and Security Policies: Establish robust policies for risk assessment and information system security.
- Incident Handling: Develop and maintain effective incident response processes.
- Business Continuity and Crisis Management: Ensure business continuity plans, backups, disaster recovery, and crisis communication strategies are in place.
- Supply Chain Security: Address cybersecurity risks in the supply chain and outsourcing.
- Secure Development and Vulnerability Management: Apply security best practices in network and information systems acquisition, development and maintenance, including handling of vulnerabilities and disclosure of security flaws.
- Effectiveness of Measures (Audit and Testing): Implement policies and procedures to assess the effectiveness of the cybersecurity measures in place.
- Basic Cyber Hygiene and Training: Promote fundamental security practices (like strong passwords, updates, secure configurations) and provide cybersecurity awareness training for staff.
- Cryptography and Encryption: Define policies on the use of cryptography, including where encryption is appropriate.
- Identity and Access Management: Enforce strict access control policies, maintain an inventory of IT assets, and ensure human resources security (e.g. employee vetting, roles and responsibilities).
- Multi-Factor Authentication (MFA) & Secure Communications: Use multi-factor or continuous authentication solutions for user access, and secure all voice, video, text, and emergency communications within the entity.
These ten areas form a comprehensive baseline. In summary, NIS2 is pushing organizations to adopt a holistic cybersecurity program – from prevention (risk management, secure development, supply chain security) to detection/response (incident handling, monitoring) to recovery (continuity plans) – and to institutionalize processes like training, access control, and regular audits of their security posture.
🚨 Incident Reporting Obligations
Beyond just handling incidents internally, NIS2 introduces detailed reporting requirements for certain cyber incidents. If an incident has a “significant impact” on the provision of an entity’s services (criteria include causing substantial disruption or financial loss, or affecting a large number of people or other organizations), it must be reported to the national authorities:
- 24-hour Early Warning: Within 24 hours of becoming aware of a significant incident, the organization must send an initial early warning notification to the Computer Security Incident Response Team (CSIRT) or competent authority, indicating if the incident might be malicious or could have cross-border impact.
- 72-hour Incident Notification: Within 72 hours of awareness, a more detailed incident report is due, providing an initial assessment of the incident’s nature, severity, impact, and (if known) indicators of compromise. This includes a granular understanding of the data affected.
- Intermediate Updates: Upon request, the entity should provide intermediate status reports to update authorities on the incident handling progress.
- One-Month Final Report: No later than one month after the initial notification, a final report must be submitted, detailing the incident’s root cause, what measures were taken to mitigate it, and any cross-border impacts identified.
These strict timelines mean organizations need well-drilled incident response teams and incident reporting procedures in place. They also need the ability to quickly assess what happened – which systems and data were affected, and what might be the cause – to meet the content requirements of the reports. Notifying affected service recipients or the public is also required in some cases (if the incident could adversely affect users or if public awareness is necessary to mitigate an ongoing threat). Under NIS2, transparency and speed in incident disclosure are not just encouraged but mandated, which is a significant shift from the more ad-hoc reporting practices of the past.
What Should Companies Be Doing Now?
Even though enforcement begins in 2026 (Q4 2025 expected for Austria), companies should not wait. IAM transformations take time — especially in distributed or hybrid environments. Here’s what your roadmap should include:
1. 🔍 Assess Your NIS2 Exposure
- Identify if you are an Essential or Important Entity (based on sector & size).
- Review the Annexes of NIS2 and national draft laws (e.g. Germany, Austria).
- Don’t forget: Even mid-sized SaaS vendors, managed service providers, or manufacturers may now be in scope.
2. 📋 Conduct a Gap Analysis
- Benchmark your current controls against NIS2 Article 21 (baseline security requirements).
- Focus on areas like Access Management, Incident Detection & Reporting, Secure Software Development, and Supply Chain Risk Management.
- Use this to prioritize gaps and build a compliance roadmap.
Tip: Use a framework like ISO/IEC 27001 or BSI IT-Grundschutz to align control maturity.
3. 🔐 Strengthen Identity & Access Management
- Enforce Least Privilege and Need-to-Know granularly at the data level.
- Automate access reviews and build audit-ready trails.
- Identify orphaned accounts, excessive permissions, and unmonitored integrations.
4. 🚨 Establish NIS2-Compliant Incident Handling
- Set up incident response procedures.
- Define roles, escalation paths, and communication protocols.
- Prepare for reporting within 24 hours (early warning), 72 hours (initial assessment) and 30 days (final report).
Practice incident simulations to test readiness across technical and executive teams.
5. 🔁 Audit & Test Cybersecurity Controls
- Schedule periodic reviews of Access Rights, Incident Response Playbooks, Backups & Business Continuity Plans.
- Use results to improve control effectiveness (a requirement under NIS2).
"Policies and procedures to assess the effectiveness of cybersecurity risk-management measures." Source: Directive (EU) 2022/2555 – Article 21
6. 🤝 Evaluate Third-Party Risks
- Inventory your vendors and outsourced service providers.
- Ensure contracts include cybersecurity clauses.
- Assess their NIS2 readiness — especially for critical integrations (e.g. cloud, identity providers, processors).
7. 💼 Engage Leadership & Assign Accountability
- CISOs should brief executive management on Compliance Obligations, Exposure Risks (e.g., penalties, liabilities), and Investments Requirements & Timelines.
- Assign internal ownership for NIS2 implementation (e.g. security, compliance, IT ops).
Involve your Data Protection Officer (DPO) or Legal Counsel to align with GDPR and regulatory communications.
8. 🗂️ Prepare Documentation & Registration
- Start preparing registration materials required by national authorities (once portals go live).
- Maintain evidence of security measures, policies, and test results.
- Track internal responsibilities and management sign-off (NIS2 mandates executive accountability).
🔧 Bridging the Gap: How CyberDesk Supports NIS2 Compliance
If you're navigating identity and access governance, CyberDesk gives you the operational muscle to comply — and prove it. As a SaaS platform purpose-built for identity-centric data access governance, CyberDesk helps you operationalize several of NIS2’s most critical obligations — not just for check-the-box compliance, but for real security maturity.
Here’s how:
✅ 1. Map Data to Identities
CyberDesk auto-classifies sensitive data (e.g. PII, customer records) and links it to human and non-human identities.
Example: Know exactly which third-party bot or contractor has access to your payroll DB.
NIS2 Article 21(2)(h): Requires access control and asset mapping.
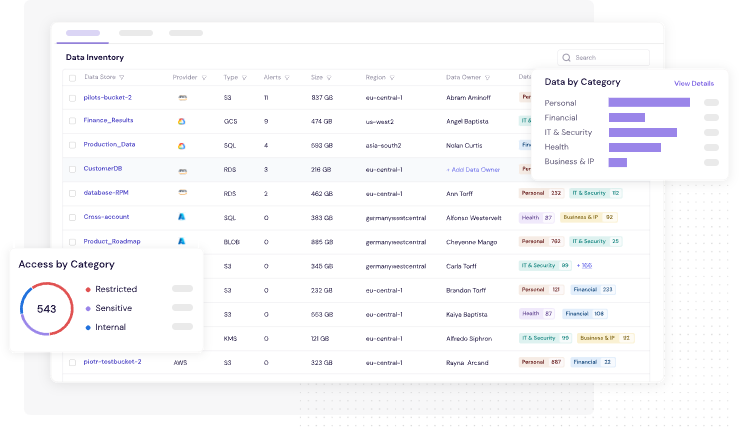
Figure 3: CyberDesk's Classification Engine Categorizes Your Organizations Data & Identities Based on Data Types and Sensitivity Levels
✅ 2. Access Graph = Real-Time Risk Visibility
CyberDesk’s Access Graph shows relationships between people, apps, and data in one glance.
Example: Spot that a dormant test account still has admin rights to your production server.
NIS2 Article 21(2)(d): Calls for risk-aware system architecture and continuous monitoring.
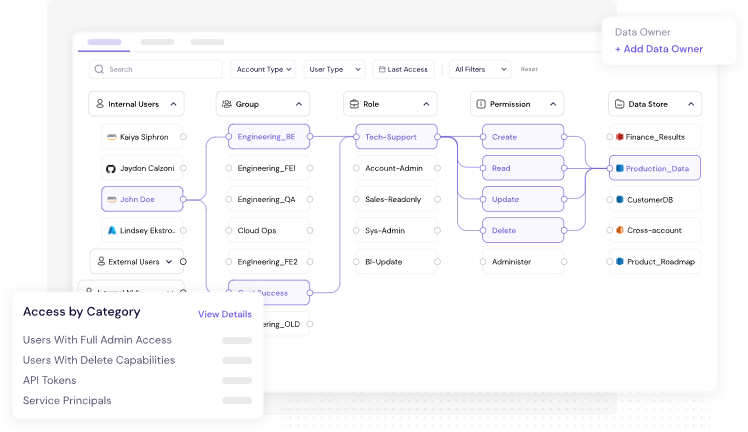
Figure 4: CyberDesk's Access Graph Provides Identity & Data Level Visibility
✅ 3. Prevent Over-Permissioning
Set and monitor for least privilege. Get alerts when access exceeds policy.
Example: An intern gaining access to sensitive HR documents = immediate alert and remediation.
NIS2 Article 21(2)(c): Focuses on incident prevention and risk limitation.
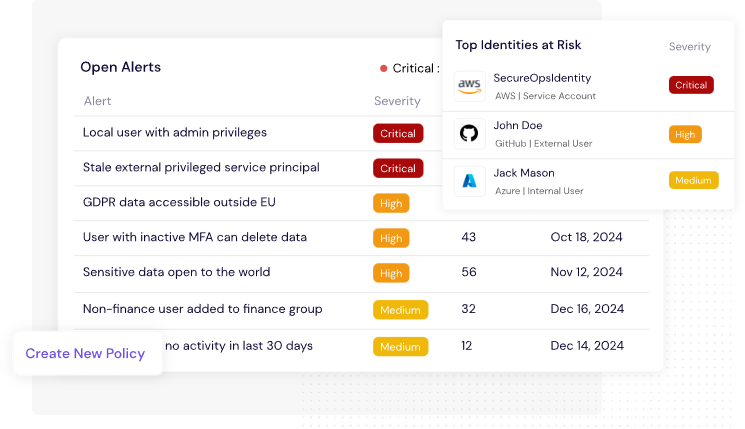
Figure 5: CyberDesk's Alerts Dashboard Facilitates Breach Risk Mitigation
✅ 4. Automated Access Reviews
Run scheduled reviews to check if users still need the access they have. Managers get smart prompts. Reviews are logged for audit.
Example: HR system access auto-review prompts quarterly approval from the HR lead. No spreadsheet needed.
NIS2 Article 21(2)(g): Requires assessing the effectiveness of cybersecurity controls.
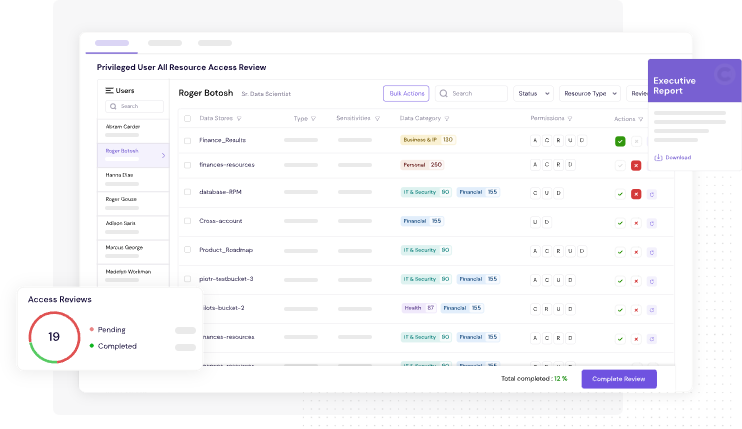
Figure 6: CyberDesk's Access Review Frees You Up From Time-Consuming Manual Processes and Helps You Stay Compliant
Final Thoughts
NIS2 is raising the bar for cybersecurity across Europe, and companies in Germany and the broader DACH region are facing a new era of regulatory expectations. The directive brings cybersecurity out of the sole domain of IT and into the boardroom by introducing accountability for top management. Achieving compliance will require organizations to adopt a more structured and measurable approach to cyber risk management — what was once considered “good practice” is now becoming law. This isn’t just a security challenge — it’s a shift in governance, accountability, and organizational resilience. That’s where CyberDesk comes in. We help you gain clarity over who has access to what, flag risks early, and operationalize NIS2 requirements through automation and visibility.
📬 Ready to see how CyberDesk fits into your security and compliance roadmap? Let’s connect.
Want to See CyberDesk in Action?
Learn how CyberDesk can help you to adaptively control who can take what actions on what data.
Founders
Dr. Tobias Lieberum & Prabhakar Mishra
Year of foundation
2022
Headquarters
Munich, Germany
About CyberDesk
Founded in 2022 and based in Munich, Germany, CyberDesk is led by Dr. Tobias Lieberum and Prabhakar Mishra. In their previous careers in sensitive environments in banking and consulting, the founders firsthand witnessed the challenges of securing data access in the cloud. In lack of a satisfactory solution, they decided to solve this global threat themselves.
For media inquiries, please contact the CyberDesk communications team
We will be happy to connect with you. Contact CyberDesk today.
Copyright © CyberDesk GmbH 2025. All rights reserved.

